Pineapple Mac OS
A standalone frontend to IPython for Mac. Get Pineapple-0.8.0 (Python 3.5, Full version). Pineapple is a self-contained application that requires no other.
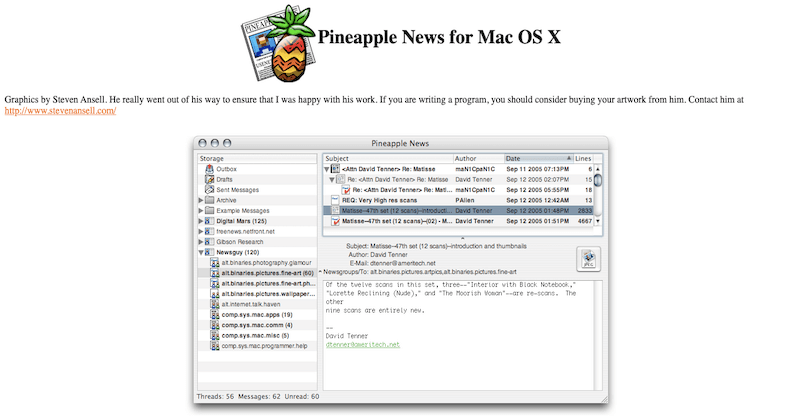
- Overview Pineapple News is a USENET newsreader for Mac OS X. It is primarily an offline reader, but it has features and user interface conventions that make it easy to use online also. As you can see, it uses the traditional three-pane paradigm.
- On Mac OS and Windows, patterns are always case-insensitive. A pattern beginning with a (?d) prefix enables removal of these files if they are preventing directory deletion. This prefix should be used by any OS generated files which you are happy to be removed. A line beginning with // is a comment and has no effect.
- 32GB Pendrive 2.0 Fruit Pineapple Model USB Flash Drive Memory Thumb Stick Gift Feature: 100% brand new and high quality Capacity: 32GB Model: Pineapple model Color: Yellow Style: Funny Reading Speed: 10MB/S Writing Speed: 4MB/S Compatibility: Supports Windows 10, Windows 8, Windows 7, Vista, ME, XP, NT Linux, and Mac OS.
SSLsplit on WiFi Pineapple
Update: after this blogpost somebody made an Infusion for SSLSplit on the WiFi Pineapple. That’s great! You can still use the howto below, but the easier way is to install the Infusion via the Pineapple bar.
Recently I was asked by a client to do a penetration test on one of their mobile apps. Fun stuff. One of the things I always test is security of the communication channel. Often SSL over HTTP is used for that. The WiFi Pineapple is a great companion for this as it provides an easy way for setting up a wireless access point with some attacks on the communication, leaving your own pentest machine free for other attacks.
Default approach to analyze traffic is to become Man-in-the-middle between App and server it communicates with. This is easily done by configuring the mobile device with a proxy (if the App communicates via a proxy aware protocol and if it accepts the system proxy settings) or to redirect traffic using iptables on the Pineapple. Than have Burp or any other proxy tool run to intercept and modify the traffic. Nothing new here.
Mac Os Download
But what was special at this specific engagement was that Burp (or any other proxy tool I know) was unable to interpreter the traffic. Yes, the iptables redirection was working, yes the SSL-mitm worked without a prob. Burp showed the initial request, and wireshark showed the traffic being forwarded to the actual server the App wanted to communicate with. But nothing was happening after that. No data, nothing. After some tinkering the hypothesis was formed that the App used non HTTP traffic over SSL and our proxy tools don’t understand it.
Pineapple Mac Strain

This is where I learned about this great tool SSLsplit. Its a proxy tool able to do full SSL certificate forging, full HTTPS decode, but also able to just show the decoded TCP and SSL traffic if it cant decode it into HTTP. Exactly what I needed! I had some compiling issues getting it to run on my Kali pentest machine. Im sure these could be fixed but I just tried installing it directly on the Pineapple. Turned out it works like a charm. Here is what you need to do:
- SSH to your Pinapple and update the packages using opkg update
- Get the OpenWRT libevent2 packages (all 5) from the official mirror at http://downloads.openwrt.org/attitude_adjustment/12.09/ar71xx/generic/packages/
- Download the unofficial OpenWRT build of SSLsplit for OpenWRT at project Ghost on Github: https://github.com/ShaPOC/ProjectGhost/blob/master/software/sslsplit/bin/sslsplit
- generate the SSL certificate authority and key for SSLsplit to use.
- openssl genrsa -out certificate.key 4096
- openssl req -new -x509 -days 365 -key certificate.key -out certificate.crt
- Depending on the config of the mobile App you may need to import the newly generated certificate.crt onto the device.
- Know what non intuitive parameters SSLsplit requires:
- mkdir /tmp/sslsplit (make a working directory)
- mkdir /tmp/sslsplit/contentlog (make a directory for session logs inside the working directory)
- ./sslsplit -k certificate.key -c certificate.crt -D -l connections.log -S /tmp/sslsplit/ -L contentlog ssl 0.0.0.0 8888
- This starts sslsplit with:
- using the cert authority we just created, used for certificate forging
- debug output to the main screen (I found this useful, you may not)
- working dir /tmp/sslsplit, duping the actual content of the connections to /tmp/sslsplit/contentlog/
- decoding traffic that comes in a port 8888 as ssl
- Redirect the traffic we want to analyze to port 8888, with a simple iptables script
- root@Pineapple:~# cat pineburp_split.sh
#!/bin/sh
echo ‘1’ > /proc/sys/net/ipv4/ip_forward
iptables -X
iptables -F
iptables -t nat -F
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
iptables -t nat -A PREROUTING -p tcp -d @@SPECIFIC_DEST_IP@@ –dport 443 -j REDIRECT –to-ports 8888 (watch it, parameters –dport and –to-ports are double dashes but for some reason WordPress displays them as one).
iptables -t nat -A POSTROUTING -j MASQUERADE
- root@Pineapple:~# cat pineburp_split.sh
- Start your app and see if it accepts the SSL certificate. In my case it did (bad for the App, good for the pentester) and the content was dumped on the pineapple in /tmp/sslsplit/contenlog with a file per TCP sessions.
Pineapple Mac Salad
Pineapple Mac And Cheese
Full SSL decode. Awesome!